ssl network extender on gentoo linux

This page describes how to get the ssl extender SNX client up and running on a linux box. This is alternative to running the Secure Remote or Mobile client on a winblows box to establih a client to gateway vpn. For configure the SSL Network Extender server, please see the VPN Administration Guide for you version of Check Point.
Contents |
install a java runtime environment JRE
google it if ya need to...
downloading snx
if you can find it on the support website, download it. I found it once, but had trouble finding it again. An alternative is to download it from the SSL gateway.
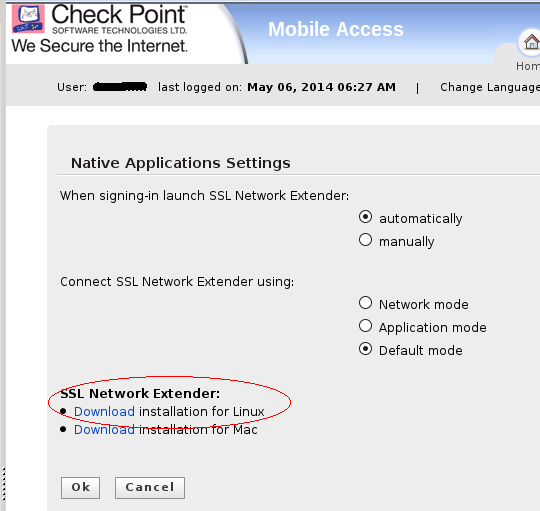
After logging into your gateway via web browser, click on settings
Then you will hopefully find a download link like this...
install SNX
run the install file. It put a binary in /usr/bin/snx for me.
The SSL gateway will likely download and try to install it for you. You may see a screen like...
Then provide your root password and it should install for you.
test run snx
Often you will receive a "failed to initialize" error message when trying to connect. If so, run it from CLI to see what error messages you get.
$ snx snx: error while loading shared libraries: libstdc++.so.5: cannot open shared object file: No such file or directory
gentoo
$ sudo emerge -av --quiet sys-libs/libstdc++-v3
for debian or ubuntu, if you can find the package...
$ dpkg -i libstdc++5_3.3.6-17ubuntu1_i386.deb
when if works, you should be able to run it and it will give you a help message like..
$ snx
failed to open file: /home/john/.snxrc
Valid attributes are:
- server SNX server to connet to
- sslport The SNX SSL port (if not default)
- username the user name
- certificate certificate file to use
- calist directory containing CA files
- reauth enable automatic reauthentication. Valid values { yes, no }
- debug enable debug output. Valid values { yes, 1-5 }
- cipher encryption algorithm to use. Valid values { RC4 / 3DES }
- proxy_name proxy hostname
- proxy_port proxy port
- proxy_user username for proxy authentication
connect to SSL gateway
Once connected you should see something like this...
and see a tun interface on you box. So, your client linux kernel must support creating tun interfaces to.
- ifconfig tunsnx /vol1/distfiles
tunsnx: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 172.16.10.41 netmask 255.255.255.255 destination 172.16.10.40
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 100 (UNSPEC)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1551 bytes 135768 (132.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Ready to use your vpn!
links
I found this very helpful...